apache tomcat慢速HTTP拒绝服务攻击安全问题解决办法
apache tomcat慢速HTTP拒绝服务攻击安全问题解决办法
问题说明:HTTP协议的设计要求服务器在处理之前完全接收到请求。如果HTTP请求未完成,或者传输速率非常低,则服务器将保持其资源占用等待剩余的数据。如果服务器占用的资源太多,则会造成拒绝服务。
漏洞危害:一台机器可在对自身带宽、无关服务和端口影响较小的情况下大量占用另一台机器的服务器资源,导致受害服务器拒绝服务。
解决方案:
1.修改配置文件server.xml,设置connectiontimeout值,默认为20000ms,修改为8000ms;
此方案修改之前,请将tomcat升级到最新版本
2.如果使用了jquery,设置ajax的请求超时时间。设置AJAX的全局timeout时间(默认为30000ms) $.ajaxSetup({timeout:8000});使用jQuery的$.ajaxSetup方法可以设置AJAX请求的默认参数选项,当程序中需要发起多个AJAX请求时,则不用再为每一个请求配置请求的参数。需要注意的是用$.ajaxSetup函数所设置的默认值不会应用到load()命令上。对于实用工具函数,如$.get()和$.post(),其HTTP方法不会因为使用这些默认值而被覆盖。设置GET的默认类型不会导致$.post()使用HTTP的GET方法。
3.如果使用了数据库连接池,则设置适当的超时时间。例如:
< Context path="/eis_zsgl" docBase="eis_zsgl" defaultSessionTimeOut="3600"
debug="5" reloadable="true" crossContext="true">
< Resource name="jdbc/eis_zsgl" auth="Container" type="javax.sql.DataSource"
maxActive="100" maxIdle="30" maxWait="10000"
username="sa" password="eisunion"
driverClassName="com.microsoft.sqlserver.jdbc.SQLServerDriver"
url="jdbc:sqlserver://127.0.0.1:1433;databasename=mytest"
validationQuery="select 1" />
< /Context>
defaultSessionTimeOut:设置会话时间 单位为秒
maxActive : 连接池的最大数据库连接数。设为0表示无限制。
maxIdle :可以同时闲置在连接池中的连接的最大数
maxWait : 最大超时时间,以毫秒计
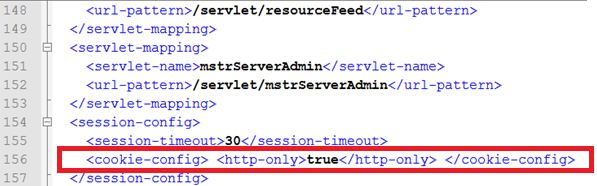
4. 如果可能,在cookie里设置httponly参数。设置Tomcat / web.xml文件:
<session-config>
<session-timeout>30</session-timeout>
<cookie-config>
<http-only>true</http-only>
<secure>true</secure>
</cookie-config>
</session-config>
Tomcat 7.0+, you can use below in web.xml as:
<session-config>
<cookie-config>
<http-only>true</http-only>
<secure>true</secure>
</cookie-config>
</session-config>
As mentioned in docs:
HttpOnly: Specifies whether any session tracking cookies created by this web application will be marked as HttpOnly
Secure: Specifies whether any session tracking cookies created by this web application will be marked as secure even if the request that initiated the corresponding session is using plain HTTP instead of HTTPS
Tomcat 7.0+, you can use below in web.xml as:
<session-config> <cookie-config> <http-only>true</http-only> <secure>true</secure> </cookie-config> </session-config>
As mentioned in docs:
HttpOnly: Specifies whether any session tracking cookies created by this web application will be marked as HttpOnly
Secure: Specifies whether any session tracking cookies created by this web application will be marked as secure even if the request that initiated the corresponding session is using plain HTTP instead of HTTPS
How to enable HTTPOnly attribute on JSESSIONID cookie for MicroStrategy Web 9.4.1 in tomcat 7
目录 返回
首页