Kubernetes RBAC 为指定用户授权访问不同命名空间权限

在开启了 TLS 的集群中,每当与集群交互的时候少不了的是身份认证,使用 kubeconfig(即证书) 和 token 两种认证方式是最简单也最通用的认证方式。
以kubectl为例介绍kubeconfig的配置。kubectl只是个go编写的可执行程序,只要为kubectl配置合适的kubeconfig,就可以在集群中的任意节点使用。kubectl默认会从$HOME/.kube目录下查找文件名为 config 的文件,也可以通过设置环境变量 KUBECONFIG 或者通过设置 --kubeconfig 去指定其它 kubeconfig 文件。
总之kubeconfig就是为访问集群所作的配置。
生成的 kubeconfig 被保存到 ~/.kube/config 文件;配置文件描述了集群、用户和上下文
Kubernetes 安全框架

k8s安全框架主要指的是apiserver,执行的kubectl命令都是向apiserver发送的请求,apiserver将这些请求持久化到etcd当中,所以apiserver是各个组件的协调者,也是集群的访问入口。
针对安全也是针对集群入口来做的,也就是apiserver,kubectl请求apiserver其实也是以http显示(http://ip:port/api/pods......)kubectl将请求给封装了,只提供给我们一些参数。
认证(Authentication)
鉴权(Authentication)
准入控制(Admission Control)
现成的插件,比如psp,imagewebhook这些都是已经存在的插件,如果需要使用,可以启用该准入控制插件。
[root@master ~]# kubectl get pod -n kube-system | grep api
kube-apiserver-master 1/1 Running 9 47h
[root@master ~]# kubectl exec kube-apiserver-master -n kube-system -- kube-apiserver -h
--enable-admission-plugins strings admission plugins that should be enabled in addition to default enabled ones (NamespaceLifecycle, LimitRanger, ServiceAccount, TaintNodesByCondition, Priority, DefaultTolerationSeconds, DefaultStorageClass, StorageObjectInUseProtection, PersistentVolumeClaimResize, RuntimeClass, CertificateApproval, CertificateSigning, CertificateSubjectRestriction, DefaultIngressClass, MutatingAdmissionWebhook, ValidatingAdmissionWebhook, ResourceQuota). Comma-delimited list of admission plugins: AlwaysAdmit, AlwaysDeny, AlwaysPullImages, CertificateApproval, CertificateSigning, CertificateSubjectRestriction, DefaultIngressClass, DefaultStorageClass, DefaultTolerationSeconds, DenyEscalatingExec, DenyExecOnPrivileged, EventRateLimit, ExtendedResourceToleration, ImagePolicyWebhook, LimitPodHardAntiAffinityTopology, LimitRanger, MutatingAdmissionWebhook, NamespaceAutoProvision, NamespaceExists, NamespaceLifecycle, NodeRestriction, OwnerReferencesPermissionEnforcement, PersistentVolumeClaimResize, PersistentVolumeLabel, PodNodeSelector, PodPreset, PodSecurityPolicy, PodTolerationRestriction, Priority, ResourceQuota, RuntimeClass, SecurityContextDeny, ServiceAccount, StorageObjectInUseProtection, TaintNodesByCondition, ValidatingAdmissionWebhook. The order of plugins in this flag does not matter.[root@master manifests]# vim kube-apiserver.yaml
- --enable-admission-plugins=NodeRestriction基于角色的权限访问控制:RBAC

k8s内置的集群角色
- cluster-admin 超级管理员,对集群所有权限(在部署dashboard的时候,先创建sa,然后将sa绑定到角色cluster-admin,最后获取到token,这就使用了内置的cluster-admin )
- admin 主要用于授权命名空间所有读写权限
- edit 允许对命名空间大多数对象读写操作,不允许查看或者修改角色、角色绑定。
- view 允许对命名空间大多数对象只读权限,不允许查看角色、角色绑定和Secret
[root@master default]#
[root@master default]# kubectl get clusterrole
NAME CREATED AT
admin 2021-05-20T07:04:01Z
edit 2021-05-20T07:04:01Z
cluster-admin 2021-05-20T07:04:01Z
view 2021-05-20T07:04:01Z上面这些角色,如果有需要就不要再去自己去创建角色,直接拿来使用即可。
to Subjects
RoleBinding 和 ClusterRoleBinding 可以将 Role 绑定到 Subjects;Subjects 可以是 groups、users 或者service accountsSubjects 中 Users 使用字符串表示,它可以是一个普通的名字字符串,如 “alice”;也可以是 email 格式的邮箱地址,如 “wangyanglinux@163.com”;甚至是一组字符串形式的数字 ID 。但是 Users 的前缀 system: 是系统保留的,集群管理员应该确保普通用户不会使用这个前缀格式Groups 书写格式与 Users 相同,都为一个字符串,并且没有特定的格式要求;同样 system: 前缀为系统保留
案例:为指定用户授权访问不同命名空间权限
示例:为lulei用户授权default命名空间Pod读取权限(只能查看,不能删除)
1. 用K8S CA签发客户端证书 基于证书的客户端认证方式
2. 生成kubeconfig授权文件 kubectl使用kubeconfig连接集群
3. 创建RBAC权限策略 做一定的权限分配
也就是生成一个kubeconfig文件,让指定用户拿着这个文件去访问集群,如何查看资源
CA签发客户端证书
(1)生成k8s客户端证书,这里面准备了CA的配置文件(用K8S CA签发客户端证书)
cat > lulei-csr.json <<EOF
{
"CN": "lulei",
这个字段相当于客户端用户信息的标识
[root@k8s-master ~]# ls /etc/kubernetes/pki/ca.crt
/etc/kubernetes/pki/ca.crtcfssl使用根证书来签发lulei客户端的证书
[root@k8s-master rbac]# cat cfssl.sh
wget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64
wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64
wget https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64
chmod +x cfssl*
mv cfssl_linux-amd64 /usr/bin/cfssl
mv cfssljson_linux-amd64 /usr/bin/cfssljson
mv cfssl-certinfo_linux-amd64 /usr/bin/cfssl-certinfo[root@k8s-master rbac]# cat cert.sh
cat > ca-config.json <<EOF
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"kubernetes": {
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
],
"expiry": "87600h"
}
}
}
}
EOF
cat > lulei-csr.json <<EOF
{
"CN": "lulei",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "k8s",
"OU": "System"
}
]
}
EOF
cfssl gencert -ca=/etc/kubernetes/pki/ca.crt -ca-key=/etc/kubernetes/pki/ca.key -config=ca-config.json -profile=kubernetes lulei-csr.json | cfssljson -bare luleiAPI Server会把客户端证书的CN字段作为User,把names.O字段作为Group。k8s在校验授权的时候就会读取这两个字段。
kubelet 使用 TLS Bootstaping 认证时,API Server 可以使用 Bootstrap Tokens 或者 Token authenticationfile 验证=token,无论哪一种,Kubenetes 都会为 token 绑定一个默认的 User 和 GroupPod使用 ServiceAccount 认证时,service-account-token 中的 JWT 会保存 User 信息有了用户信息,再创建一对角色/角色绑定(集群角色/集群角色绑定)资源对象,就可以完成权限绑定了
[root@k8s-master rbac]# ls
lulei-key.pem lulei.pem上面就是客户端证书,有多个用户需要生成多个
- lulei-key.pem 私钥 类似配置nginx https访问 .key私钥
- lulei.pem 数字证书 类似配置nginx https访问的 .crt证书
注意这里要指定k8s根证书的,kubeadm部署的话根证书默认在/etc/kubernetes/pki/
[root@k8s-master rbac]# ls /etc/kubernetes/pki/
apiserver.crt apiserver-kubelet-client.crt etcd front-proxy-client.key
apiserver-etcd-client.crt apiserver-kubelet-client.key front-proxy-ca.crt sa.key
apiserver-etcd-client.key ca.crt front-proxy-ca.key sa.pub
apiserver.key ca.key front-proxy-client.crt上面就是生成了根证书的配置文件ca-config.json,再生成为某个用户颁发的客户端请求文件。最后就是使用cfssl工具指定相关的文件去生成客户端所需要的证书。每个用户的客户端证书都是这样生成的。唯一需要区分的就是CN字段的用户名。
生成kubeconfig授权文件
集群参数设置
使用kubectl config这条命令生成kubeconfig证书,逐步生成kubeconfig里面的信息
生成证书的格式和家目录的config内容是一样的
[root@k8s-master ~]# cd .kube/
[root@k8s-master .kube]# ls
cache config这里填充了cluster的信息
kubectl config set-cluster kubernetes \
--certificate-authority=/etc/kubernetes/pki/ca.crt \
--embed-certs=true \
--server=https://192.168.179.102:6443 \
--kubeconfig=lulei.kubeconfig
[root@k8s-master rbac]# kubectl config set-cluster kubernetes \
> --certificate-authority=/etc/kubernetes/pki/ca.crt \
> --embed-certs=true \
> --server=https://192.168.179.102:6443 \
> --kubeconfig=lulei.kubeconfig
Cluster "kubernetes" set.
这里生成了文件
[root@k8s-master rbac]# cat lulei.kubeconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01URXhOVEEyTlRZeU5sb1hEVE13TVRFeE16QTJOVFl5Tmxvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBSmZsCmtaVVhUcVJ3ZjJVeDdqS1pjQURvaHV1aHNXcHAvK2NIOEF1MVpmR3JqN0lTb3VoelVISkZ5cGR5ekdoTDFBRHgKMTkxVlVCN1ZCWlk4cXBDRHYyRnZvWkRFbFVYR1JrTFFDT0lxc1hOVUt3ZU0xdnJqZnpZVW5ZNGN6NDhKNDdpTgpnUjJHRGtsWUlrZFpGZEU1ekN2eitldEtEVVUzdE5GV0djL00yZFE0NUIxNGZlTldpTUR3T0l3dTBSSWRvYmpnCndmSnhoVlJHMmgzdEplL0RpUjQ2cXI1NEdMVUU2VXNDUGJvZ0JxNTVBakt2c2NiOWUzeGdzMVJhZW1BdFZhd08KSFNjRkRDYWhBZDVPUlgzMlIzSGNoRnY2QmFwczgyb0dqUDBLOEY1RXNQWkFYQXFoK3c0UTFMRWQ2aHRuQWhyWAoxcmJ5cTF4eUNESnhhbENaSHBjQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZPZXFad29TeUxrVDVKWXlRNURMamUzRFRHUjJNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFCemtMRXMzUGhIN08wYWs5VWlTbFhDVTljK1RoYlZaTmZVUStKS1JpQU5KQys5Qm8vZApLdUlLYWhxQlE5UkprSk53TmVwT0NJOWxzcGJ4TGtHK3ArYktHV29Yb25CME5RdnZoZTRQd0p0dmdUcGlhVmVYCmNLejhUMDBRT1YyRzR0WEtmaTViK0dvZDA3NktlZm4zbm00U0l1VDh6bmNDclUxeHRpQTRSU3RQRVZZZTRQalAKY2p6MHJVS3BnTmhJL0lYc2JPVDNYV0hFNE4vU0VLcmtIYkRJNFpEUGRYa2gxd3piM1FZODFuZTh1enBNQVJ5VwpLbkx6R1NRaGJ0WTlWRUZkdlhGK0wreWFrQjcrR29xa1lJa1BNdURveFRoeTBuMFJjZStSTUhtZkFQSEh2RDFyCjdSNC9xdlpBLzA4Q0hxb3ZDcCsxUzNXbFE5WE5MRzE3TWExTAotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://192.168.179.102:6443
name: kubernetes
contexts: null
current-context: ""
kind: Config
preferences: {}
users: null本段设置了所需要访问的集群的信息。
- 使用set-cluster设置了需要访问的集群,如上为kubernetes,这只是个名称,实际为--server指向的apiserver
- --certificate-authority设置了该集群的公钥
- --embed-certs为true表示将--certificate-authority证书写入到kubeconfig中
- --server则表示该集群的kube-apiserver地址
生成的kubeconfig 被保存到 lulei.kubeconfig文件
用户参数设置
kubectl config set-credentials lulei \
--client-key=lulei-key.pem \
--client-certificate=lulei.pem \
--embed-certs=true \
--kubeconfig=lulei.kubeconfig
[root@k8s-master rbac]# kubectl config set-credentials lulei \
> --client-key=lulei-key.pem \
> --client-certificate=lulei.pem \
> --embed-certs=true \
> --kubeconfig=lulei.kubeconfig
User "lulei" set.
[root@k8s-master rbac]# cat lulei.kubeconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01URXhOVEEyTlRZeU5sb1hEVE13TVRFeE16QTJOVFl5Tmxvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBSmZsCmtaVVhUcVJ3ZjJVeDdqS1pjQURvaHV1aHNXcHAvK2NIOEF1MVpmR3JqN0lTb3VoelVISkZ5cGR5ekdoTDFBRHgKMTkxVlVCN1ZCWlk4cXBDRHYyRnZvWkRFbFVYR1JrTFFDT0lxc1hOVUt3ZU0xdnJqZnpZVW5ZNGN6NDhKNDdpTgpnUjJHRGtsWUlrZFpGZEU1ekN2eitldEtEVVUzdE5GV0djL00yZFE0NUIxNGZlTldpTUR3T0l3dTBSSWRvYmpnCndmSnhoVlJHMmgzdEplL0RpUjQ2cXI1NEdMVUU2VXNDUGJvZ0JxNTVBakt2c2NiOWUzeGdzMVJhZW1BdFZhd08KSFNjRkRDYWhBZDVPUlgzMlIzSGNoRnY2QmFwczgyb0dqUDBLOEY1RXNQWkFYQXFoK3c0UTFMRWQ2aHRuQWhyWAoxcmJ5cTF4eUNESnhhbENaSHBjQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZPZXFad29TeUxrVDVKWXlRNURMamUzRFRHUjJNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFCemtMRXMzUGhIN08wYWs5VWlTbFhDVTljK1RoYlZaTmZVUStKS1JpQU5KQys5Qm8vZApLdUlLYWhxQlE5UkprSk53TmVwT0NJOWxzcGJ4TGtHK3ArYktHV29Yb25CME5RdnZoZTRQd0p0dmdUcGlhVmVYCmNLejhUMDBRT1YyRzR0WEtmaTViK0dvZDA3NktlZm4zbm00U0l1VDh6bmNDclUxeHRpQTRSU3RQRVZZZTRQalAKY2p6MHJVS3BnTmhJL0lYc2JPVDNYV0hFNE4vU0VLcmtIYkRJNFpEUGRYa2gxd3piM1FZODFuZTh1enBNQVJ5VwpLbkx6R1NRaGJ0WTlWRUZkdlhGK0wreWFrQjcrR29xa1lJa1BNdURveFRoeTBuMFJjZStSTUhtZkFQSEh2RDFyCjdSNC9xdlpBLzA4Q0hxb3ZDcCsxUzNXbFE5WE5MRzE3TWExTAotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://192.168.179.102:6443
name: kubernetes
contexts: null
current-context: ""
kind: Config
preferences: {}
users:
- name: lulei
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURnakNDQW1xZ0F3SUJBZ0lVYVVuc3VhVnA1WkxVRnNmcXk2TWRaNGRQR0pFd0RRWUpLb1pJaHZjTkFRRUwKQlFBd0ZURVRNQkVHQTFVRUF4TUthM1ZpWlhKdVpYUmxjekFlRncweU1UQXhNVGd3T0RRd01EQmFGdzB6TVRBeApNVFl3T0RRd01EQmFNR0F4Q3pBSkJnTlZCQVlUQWtOT01SQXdEZ1lEVlFRSUV3ZENaV2xLYVc1bk1SQXdEZ1lEClZRUUhFd2RDWldsS2FXNW5NUXd3Q2dZRFZRUUtFd05yT0hNeER6QU5CZ05WQkFzVEJsTjVjM1JsYlRFT01Bd0cKQTFVRUF4TUZiSFZzWldrd2dnRWlNQTBHQ1NxR1NJYjNEUUVCQVFVQUE0SUJEd0F3Z2dFS0FvSUJBUUNZNWM2Kwo0bFZIbTJvMXR6bHcyd3dncFp1Sjd2RnJ3TWVtMUlqSkg2c1ZTSE92NnJBOStjUUFmYk50N0swM0NHa2JhVlh5ClJ0ejh6RitYL3BhZUNmZW8wNnFKcU5RZkVhMllQc1lyREZkdXRRdUNGSmpxdlBrbWN3TDdGdnVGcGlsNDZ4TkoKQ2s2QWpXNzh2TUNKQWx2dEtWcWdQdXFyd1lDTkNvZ0NWUEF0cTZMZ2x6b0UwOU9jL05wY2hzdHZwdzR5QTVPcwp0SkkzcDRXbUZQSWNYZUNvR3BlMzk3WUJ3b1JnVDlMVHlnTzhXUkpBeEpQRUFsRnc1KzJqcEZnaU5BdC9tMmFICkFNcXc1MjZRVnVsMnFWYjJyOXViU1drRzFLWS9Va09jOW4zbFgyYnRPWTN2NWxFVUx3cHozYmZwY2lDTE1yN3EKZTB4Sml1TWpicEVNTnpTVkFnTUJBQUdqZnpCOU1BNEdBMVVkRHdFQi93UUVBd0lGb0RBZEJnTlZIU1VFRmpBVQpCZ2dyQmdFRkJRY0RBUVlJS3dZQkJRVUhBd0l3REFZRFZSMFRBUUgvQkFJd0FEQWRCZ05WSFE0RUZnUVVhc0orCmw2ai9JdGxObytrOGVRRDVlSzNTNWN3d0h3WURWUjBqQkJnd0ZvQVU1NnBuQ2hMSXVSUGtsakpEa011TjdjTk0KWkhZd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFCNjdSVm00U0c4MUZtMnZqSmQ4S1crdk5CMzZESC9tZGZCQwpWRUovdmRiS09JL0dmalc1bXdvckhtVHZyNmJRVE15U1NWMUFZd3RDZzRzNVZhUWJqOXJzUU1TNmZVcnlnaGdqCi9YZkxVVTBkOE1jTTZkMEZpM1h1c3FnVTZjNDBTcHozRkxUZ3BBUUU4Z2Z3aTdUbmRUcHJjU3hMaHV3S0RtVEIKMG5jK0U5TCtlOW5meTliVUp2akZSUGpKV1Q2Z3hEamhJZi9CK0g1andiY1NCM0x6KzBoQzkzaUVkbDdocWlLUwpiMExNSmIvYjZaN1Vya0FEQlR0WlVJWFFWb2lSdnRXWmhCUktKZC9PVWlZWW5CbEpmYnJmYUM4UFNtTHpPak53CnBhaFBzaWZCekplZnRlU1BPZmFZZXhKNUVGSVdLV1lLWnYzY09jQjViSFlYS3p2dWlXUT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBbU9YT3Z1SlZSNXRxTmJjNWNOc01JS1diaWU3eGE4REhwdFNJeVIrckZVaHpyK3F3ClBmbkVBSDJ6YmV5dE53aHBHMmxWOGtiYy9NeGZsLzZXbmduM3FOT3FpYWpVSHhHdG1EN0dLd3hYYnJVTGdoU1kKNnJ6NUpuTUMreGI3aGFZcGVPc1RTUXBPZ0kxdS9MekFpUUpiN1NsYW9EN3FxOEdBalFxSUFsVHdMYXVpNEpjNgpCTlBUblB6YVhJYkxiNmNPTWdPVHJMU1NONmVGcGhUeUhGM2dxQnFYdC9lMkFjS0VZRS9TMDhvRHZGa1NRTVNUCnhBSlJjT2Z0bzZSWUlqUUxmNXRtaHdES3NPZHVrRmJwZHFsVzlxL2JtMGxwQnRTbVAxSkRuUFo5NVY5bTdUbU4KNytaUkZDOEtjOTIzNlhJZ2l6Sys2bnRNU1lyakkyNlJERGMwbFFJREFRQUJBb0lCQUZFMC9YSDAxRWFNRFFVcQpvNStGT0JPKzRiV0k2MERIeTBLWWIyNGpHOExhRUZmRzFvU1VPNzNuQlgzRXp0c0Q1STlpaXZ0N0Y3Uk0rQmpLClowVFpGbWpjd3g4S1JGK2NEQTlvaCtnbFRlckd6YTN4TXFhNlo3bzhLOEVnbThhSVVrNmV6RWRtNmZydEk1Mm8Kd3JvQ1BzRGZ6ZnArY0RWNU9NV3dhanlTMEYzd2tRYmloVmdmckxLdCtkUEJrV2ZMWjljd3FUYmFZMzZSb202eApHdGY1eWM1ZnZnZ0E0Z3FndjBaSW9OelMzQytNK0JBdGpzWDRUOVFJL09ZcmxsWHJXVksvRVRDTFRYUGhIS1cvCnk5OUNrU3I2ZWR2ODJsbmQ0VGFPVE9pRWp1eVhMVkFCOWVFeWZnUXhLNmJTck1JaFNINTl3M0liaEpWZkU0S3oKVEZsd0V3RUNnWUVBeWF0bW1ESXAyLzhaNHJtcjkvc2RlNUF3Y0d3Q3BxNGdKRkVaR3BoallpMlFPVVRsNnNMNApDNFpjMER6YWN4VzFuUzZHSWF6cTFrdVAwcWVhNVlpV1lPWmFmekdKeXp6L083VGRyRUF6bTcxaDdHL1FSS1gwCllhSGxsYTNGY0FYTEdmZ3ZOeW8xTTJmZUEzOUZiWDczWUF6OGlRa05KUXpnUlFuRzFJN1I2SjBDZ1lFQXdoYSsKd0ZjQ3FIYXVjNWZUeVZOQ1V1Ujd3disyWDluY3plSkl5aGUrTzFnckZGRVIxblVUdGRCTSttNFRWSjZSd0F6MwpVY05CY3JOQXpJK1l2ZGR3OUxCQmhadTkrRmJwTWV5ZkR6V0hyR282NVBHSE4yUm5raElhR3dia1pNUnBHYWhECmJTcDZHK3JzMUMzYkMxMjU3SElwdVFlQlp4R1NJb2VEUTZtYnpsa0NnWUJ3UHh0YWFNbE5ycDQ4eUhWRUVCdm4KMDJoeW1sdWJaRjExZVVJTXdIYkloVzI1d25ScUIxekNKV1h4YlgxMUFzZFVGam9IOGxPL05NMTNSVng4bDFxRAowcExhS3J0MFNKNFRJR2NsWVpLWUEzL0dkckdvRStxQ2tQYlZLYVF6NXJXVjNjS0I1TmM1cG4wMjJ4Yk1qQmVwCitYQng0WHpVZTJjMFplMnFEMWdjTFFLQmdDNy9ETzlMNGxQaWNQbUNjUURWelVCL0hNeXAySUk3SWJFa3N0VmsKakdhWVFjNG9sellqb1VNc0RnZXhzYktTdHQ0WEJhZmhySzVXWTBGbEgrb1FDY1RtRE9lS1A2U3Jmc25jN3VMaQo1bGhFWE1CbEQ0WEZKU01FaVJlMFFvZDMyNjhmeER2aHhqR09ZQXc4a2thZFNsRExqL2pDclgzRWptc1gveHZhCkxPVDVBb0dCQUw0azE0NVdnQlRCOWZRY05iOE01SXNNZmx1QzhHc2FNbDgzQnU3T2x6T3lLanFMbGxSdzlIc2QKbXVEZVJwNmxIRmlDWHhZdXRQWTRPd2NFbndBWDcyRHRlUzJ5bnBjSUNYTTVTbkEvWlJEeDZOZnlWMWNsb1Zlagprd3grc09mT3pBeXNnN21TS1ZxMkVEZThKU1pFOUpEVCswbm5zaHd5bm5hdXZpbk8zZEF4Ci0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==本段主要设置用户的相关信息,主要是用户证书。如上的用户名为lulei,证书为:lulei.pem,私钥为:lulei-key.pem。注意客户端的证书首先要经过集群CA的签署,否则不会被集群认可。此处使用的是ca认证方式,也可以使用token认证,如kubelet的 TLS Boostrap机制下的bootstrapping使用的就是token认证方式。上述kubectl使用的是ca认证,不需要token字段
上下文参数
kubectl config set-context kubernetes \
--cluster=kubernetes \
--user=lulei \
--kubeconfig=lulei.kubeconfig
# 设置上下文参数
[root@k8s-master rbac]# kubectl config set-context kubernetes \
> --cluster=kubernetes \
> --user=lulei \
> --kubeconfig=lulei.kubeconfig
Context "kubernetes" created.
[root@k8s-master rbac]# cat lulei.kubeconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01URXhOVEEyTlRZeU5sb1hEVE13TVRFeE16QTJOVFl5Tmxvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBSmZsCmtaVVhUcVJ3ZjJVeDdqS1pjQURvaHV1aHNXcHAvK2NIOEF1MVpmR3JqN0lTb3VoelVISkZ5cGR5ekdoTDFBRHgKMTkxVlVCN1ZCWlk4cXBDRHYyRnZvWkRFbFVYR1JrTFFDT0lxc1hOVUt3ZU0xdnJqZnpZVW5ZNGN6NDhKNDdpTgpnUjJHRGtsWUlrZFpGZEU1ekN2eitldEtEVVUzdE5GV0djL00yZFE0NUIxNGZlTldpTUR3T0l3dTBSSWRvYmpnCndmSnhoVlJHMmgzdEplL0RpUjQ2cXI1NEdMVUU2VXNDUGJvZ0JxNTVBakt2c2NiOWUzeGdzMVJhZW1BdFZhd08KSFNjRkRDYWhBZDVPUlgzMlIzSGNoRnY2QmFwczgyb0dqUDBLOEY1RXNQWkFYQXFoK3c0UTFMRWQ2aHRuQWhyWAoxcmJ5cTF4eUNESnhhbENaSHBjQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZPZXFad29TeUxrVDVKWXlRNURMamUzRFRHUjJNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFCemtMRXMzUGhIN08wYWs5VWlTbFhDVTljK1RoYlZaTmZVUStKS1JpQU5KQys5Qm8vZApLdUlLYWhxQlE5UkprSk53TmVwT0NJOWxzcGJ4TGtHK3ArYktHV29Yb25CME5RdnZoZTRQd0p0dmdUcGlhVmVYCmNLejhUMDBRT1YyRzR0WEtmaTViK0dvZDA3NktlZm4zbm00U0l1VDh6bmNDclUxeHRpQTRSU3RQRVZZZTRQalAKY2p6MHJVS3BnTmhJL0lYc2JPVDNYV0hFNE4vU0VLcmtIYkRJNFpEUGRYa2gxd3piM1FZODFuZTh1enBNQVJ5VwpLbkx6R1NRaGJ0WTlWRUZkdlhGK0wreWFrQjcrR29xa1lJa1BNdURveFRoeTBuMFJjZStSTUhtZkFQSEh2RDFyCjdSNC9xdlpBLzA4Q0hxb3ZDcCsxUzNXbFE5WE5MRzE3TWExTAotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://192.168.179.102:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: lulei
name: kubernetes
current-context: ""
kind: Config
preferences: {}
users:
- name: lulei
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURnakNDQW1xZ0F3SUJBZ0lVYVVuc3VhVnA1WkxVRnNmcXk2TWRaNGRQR0pFd0RRWUpLb1pJaHZjTkFRRUwKQlFBd0ZURVRNQkVHQTFVRUF4TUthM1ZpWlhKdVpYUmxjekFlRncweU1UQXhNVGd3T0RRd01EQmFGdzB6TVRBeApNVFl3T0RRd01EQmFNR0F4Q3pBSkJnTlZCQVlUQWtOT01SQXdEZ1lEVlFRSUV3ZENaV2xLYVc1bk1SQXdEZ1lEClZRUUhFd2RDWldsS2FXNW5NUXd3Q2dZRFZRUUtFd05yT0hNeER6QU5CZ05WQkFzVEJsTjVjM1JsYlRFT01Bd0cKQTFVRUF4TUZiSFZzWldrd2dnRWlNQTBHQ1NxR1NJYjNEUUVCQVFVQUE0SUJEd0F3Z2dFS0FvSUJBUUNZNWM2Kwo0bFZIbTJvMXR6bHcyd3dncFp1Sjd2RnJ3TWVtMUlqSkg2c1ZTSE92NnJBOStjUUFmYk50N0swM0NHa2JhVlh5ClJ0ejh6RitYL3BhZUNmZW8wNnFKcU5RZkVhMllQc1lyREZkdXRRdUNGSmpxdlBrbWN3TDdGdnVGcGlsNDZ4TkoKQ2s2QWpXNzh2TUNKQWx2dEtWcWdQdXFyd1lDTkNvZ0NWUEF0cTZMZ2x6b0UwOU9jL05wY2hzdHZwdzR5QTVPcwp0SkkzcDRXbUZQSWNYZUNvR3BlMzk3WUJ3b1JnVDlMVHlnTzhXUkpBeEpQRUFsRnc1KzJqcEZnaU5BdC9tMmFICkFNcXc1MjZRVnVsMnFWYjJyOXViU1drRzFLWS9Va09jOW4zbFgyYnRPWTN2NWxFVUx3cHozYmZwY2lDTE1yN3EKZTB4Sml1TWpicEVNTnpTVkFnTUJBQUdqZnpCOU1BNEdBMVVkRHdFQi93UUVBd0lGb0RBZEJnTlZIU1VFRmpBVQpCZ2dyQmdFRkJRY0RBUVlJS3dZQkJRVUhBd0l3REFZRFZSMFRBUUgvQkFJd0FEQWRCZ05WSFE0RUZnUVVhc0orCmw2ai9JdGxObytrOGVRRDVlSzNTNWN3d0h3WURWUjBqQkJnd0ZvQVU1NnBuQ2hMSXVSUGtsakpEa011TjdjTk0KWkhZd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFCNjdSVm00U0c4MUZtMnZqSmQ4S1crdk5CMzZESC9tZGZCQwpWRUovdmRiS09JL0dmalc1bXdvckhtVHZyNmJRVE15U1NWMUFZd3RDZzRzNVZhUWJqOXJzUU1TNmZVcnlnaGdqCi9YZkxVVTBkOE1jTTZkMEZpM1h1c3FnVTZjNDBTcHozRkxUZ3BBUUU4Z2Z3aTdUbmRUcHJjU3hMaHV3S0RtVEIKMG5jK0U5TCtlOW5meTliVUp2akZSUGpKV1Q2Z3hEamhJZi9CK0g1andiY1NCM0x6KzBoQzkzaUVkbDdocWlLUwpiMExNSmIvYjZaN1Vya0FEQlR0WlVJWFFWb2lSdnRXWmhCUktKZC9PVWlZWW5CbEpmYnJmYUM4UFNtTHpPak53CnBhaFBzaWZCekplZnRlU1BPZmFZZXhKNUVGSVdLV1lLWnYzY09jQjViSFlYS3p2dWlXUT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBbU9YT3Z1SlZSNXRxTmJjNWNOc01JS1diaWU3eGE4REhwdFNJeVIrckZVaHpyK3F3ClBmbkVBSDJ6YmV5dE53aHBHMmxWOGtiYy9NeGZsLzZXbmduM3FOT3FpYWpVSHhHdG1EN0dLd3hYYnJVTGdoU1kKNnJ6NUpuTUMreGI3aGFZcGVPc1RTUXBPZ0kxdS9MekFpUUpiN1NsYW9EN3FxOEdBalFxSUFsVHdMYXVpNEpjNgpCTlBUblB6YVhJYkxiNmNPTWdPVHJMU1NONmVGcGhUeUhGM2dxQnFYdC9lMkFjS0VZRS9TMDhvRHZGa1NRTVNUCnhBSlJjT2Z0bzZSWUlqUUxmNXRtaHdES3NPZHVrRmJwZHFsVzlxL2JtMGxwQnRTbVAxSkRuUFo5NVY5bTdUbU4KNytaUkZDOEtjOTIzNlhJZ2l6Sys2bnRNU1lyakkyNlJERGMwbFFJREFRQUJBb0lCQUZFMC9YSDAxRWFNRFFVcQpvNStGT0JPKzRiV0k2MERIeTBLWWIyNGpHOExhRUZmRzFvU1VPNzNuQlgzRXp0c0Q1STlpaXZ0N0Y3Uk0rQmpLClowVFpGbWpjd3g4S1JGK2NEQTlvaCtnbFRlckd6YTN4TXFhNlo3bzhLOEVnbThhSVVrNmV6RWRtNmZydEk1Mm8Kd3JvQ1BzRGZ6ZnArY0RWNU9NV3dhanlTMEYzd2tRYmloVmdmckxLdCtkUEJrV2ZMWjljd3FUYmFZMzZSb202eApHdGY1eWM1ZnZnZ0E0Z3FndjBaSW9OelMzQytNK0JBdGpzWDRUOVFJL09ZcmxsWHJXVksvRVRDTFRYUGhIS1cvCnk5OUNrU3I2ZWR2ODJsbmQ0VGFPVE9pRWp1eVhMVkFCOWVFeWZnUXhLNmJTck1JaFNINTl3M0liaEpWZkU0S3oKVEZsd0V3RUNnWUVBeWF0bW1ESXAyLzhaNHJtcjkvc2RlNUF3Y0d3Q3BxNGdKRkVaR3BoallpMlFPVVRsNnNMNApDNFpjMER6YWN4VzFuUzZHSWF6cTFrdVAwcWVhNVlpV1lPWmFmekdKeXp6L083VGRyRUF6bTcxaDdHL1FSS1gwCllhSGxsYTNGY0FYTEdmZ3ZOeW8xTTJmZUEzOUZiWDczWUF6OGlRa05KUXpnUlFuRzFJN1I2SjBDZ1lFQXdoYSsKd0ZjQ3FIYXVjNWZUeVZOQ1V1Ujd3disyWDluY3plSkl5aGUrTzFnckZGRVIxblVUdGRCTSttNFRWSjZSd0F6MwpVY05CY3JOQXpJK1l2ZGR3OUxCQmhadTkrRmJwTWV5ZkR6V0hyR282NVBHSE4yUm5raElhR3dia1pNUnBHYWhECmJTcDZHK3JzMUMzYkMxMjU3SElwdVFlQlp4R1NJb2VEUTZtYnpsa0NnWUJ3UHh0YWFNbE5ycDQ4eUhWRUVCdm4KMDJoeW1sdWJaRjExZVVJTXdIYkloVzI1d25ScUIxekNKV1h4YlgxMUFzZFVGam9IOGxPL05NMTNSVng4bDFxRAowcExhS3J0MFNKNFRJR2NsWVpLWUEzL0dkckdvRStxQ2tQYlZLYVF6NXJXVjNjS0I1TmM1cG4wMjJ4Yk1qQmVwCitYQng0WHpVZTJjMFplMnFEMWdjTFFLQmdDNy9ETzlMNGxQaWNQbUNjUURWelVCL0hNeXAySUk3SWJFa3N0VmsKakdhWVFjNG9sellqb1VNc0RnZXhzYktTdHQ0WEJhZmhySzVXWTBGbEgrb1FDY1RtRE9lS1A2U3Jmc25jN3VMaQo1bGhFWE1CbEQ0WEZKU01FaVJlMFFvZDMyNjhmeER2aHhqR09ZQXc4a2thZFNsRExqL2pDclgzRWptc1gveHZhCkxPVDVBb0dCQUw0azE0NVdnQlRCOWZRY05iOE01SXNNZmx1QzhHc2FNbDgzQnU3T2x6T3lLanFMbGxSdzlIc2QKbXVEZVJwNmxIRmlDWHhZdXRQWTRPd2NFbndBWDcyRHRlUzJ5bnBjSUNYTTVTbkEvWlJEeDZOZnlWMWNsb1Zlagprd3grc09mT3pBeXNnN21TS1ZxMkVEZThKU1pFOUpEVCswbm5zaHd5bm5hdXZpbk8zZEF4Ci0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==集群参数和用户参数可以同时设置多对,在上下文参数中将集群参数和用户参数关联起来。上面的上下文名称为kubenetes,集群为kubenetes,用户为lulei,表示使用lulei的用户凭证来访问kubenetes集群的default命名空间,也可以增加--namspace来指定访问的命名空间。
最后使用kubectl config use-context kubernetes来使用名为kubenetes的环境项来作为配置。如果配置了多个环境项,可以通过切换不同的环境项名字来访问到不同的集群环境。
# 设置当前使用配置
kubectl config use-context kubernetes --kubeconfig=lulei.kubeconfig
[root@k8s-master rbac]# kubectl config use-context kubernetes --kubeconfig=lulei.kubeconfig
Switched to context "kubernetes".
contexts:
- context:
cluster: kubernetes
user: lulei
name: kubernetes
current-context: kubernetes
kind: Config
preferences: {}可以看到上面配置是没有问题的,给出的提示是用户lulei是不能列出这方面资源的
[root@k8s-master rbac]# kubectl --kubeconfig=lulei.kubeconfig get pod
Error from server (Forbidden): pods is forbidden: User "lulei" cannot list resource "pods" in API group "" in the namespace "default"可以看到通过管理员的配置文件是可以访问到的
[root@k8s-master rbac]# kubectl --kubeconfig=/root/.kube/config get pod
NAME READY STATUS RESTARTS AGE
nginx-6799fc88d8-drb2s 1/1 Running 3 64d上面说明了配置文件是没有问题的,只是缺少相应的权限
创建RBAC权限策略
需要创建role和rolebinding,role是权限的集合,rolebinding是要将role里面权限绑定到指定的用户,也就是我们上面的lulei用户
比较常见的授权维度:
• user:用户名
• group:用户分组
• 资源,例如pod、deployment
• 资源操作方法:get,list,create,update,patch,watch,delete
• 命名空间
• API组

组可以通过kubectl api-resources查看k8s当中所有资源,并且资源属于哪个组
[root@master tls]# kubectl api-resources
NAME SHORTNAMES APIGROUP NAMESPACED KIND
bindings true Binding
componentstatuses cs false ComponentStatus
configmaps cm true ConfigMap
endpoints ep true Endpoints
events ev true Event
limitranges limits true LimitRange
namespaces ns false Namespace
nodes no false Node
persistentvolumeclaims pvc true
#查看deployment属于apps组
[root@master tls]# kubectl api-resources | grep deployment
deployments deploy apps true Deployment
[root@master tls]# kubectl --kubeconfig=lulei.kubeconfig get deployment
Error from server (Forbidden): deployments.apps is forbidden: User "lulei" cannot list resource "deployments" in API group "apps" in the namespace "default"
rules:
- apiGroups: ["","apps"]
resources: ["pods","deployments"]
verbs: ["get", "watch", "list"]
[root@master tls]# kubectl apply -f rbac.yaml
role.rbac.authorization.k8s.io/pod-reader configured
[root@master tls]# kubectl --kubeconfig=lulei.kubeconfig get deployment
NAME READY UP-TO-DATE AVAILABLE AGE
nfs-client-provisioner 1/1 1 1 40d
#ingress属于networking.k8s.io这个组
[root@master tls]# kubectl api-resources | grep ingress
ingresses ing extensions true Ingress
ingressclasses networking.k8s.io false IngressClass
ingresses ing networking.k8s.io true Ingress
[root@k8s-master rbac]# cat rbac.yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: pod-reader
rules: #配置授权维度
- apiGroups: [""] #里面为空,为核心的api组,常用的资源都在核心组里面
resources: ["pods"]
verbs: ["get", "watch", "list"] #资源操作方法
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: read-pods
namespace: default
subjects:
- kind: User
name: lulei
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: Role
name: pod-reader
apiGroup: rbac.authorization.k8s.io
[root@k8s-master rbac]# kubectl apply -f rbac.yaml
role.rbac.authorization.k8s.io/pod-reader created
rolebinding.rbac.authorization.k8s.io/read-pods createdname: lulei 和CN里面名字对应,上面绑定有两块,主题即绑定谁,另外和哪个role绑定
[root@k8s-master rbac]# kubectl --kubeconfig=lulei.kubeconfig get pod
NAME READY STATUS RESTARTS AGE
nginx-6799fc88d8-drb2s 1/1 Running 3 64d
[root@k8s-master rbac]# kubectl --kubeconfig=lulei.kubeconfig get deployment
Error from server (Forbidden): deployments.apps is forbidden: User "lulei" cannot list resource "deployments" in API group "apps" in the namespace "default"现在准确授权了,只能查看Pod,其他资源不能查看
删除也不行
[root@k8s-master rbac]# kubectl --kubeconfig=lulei.kubeconfig delete pod nginx-6799fc88d8-drb2s
Error from server (Forbidden): pods "nginx-6799fc88d8-drb2s" is forbidden: User "lulei" cannot delete resource "pods" in API group "" in the namespace "default"现在要放开权限
授权的时候还要考虑资源在不在这个组里面,apps里面包含了deployment
[root@k8s-master rbac]# cat rbac.yml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: pod-reader
rules:
- apiGroups: ["","apps"]
resources: ["pods","deployments","services"]
verbs: ["get", "watch", "list"] [root@k8s-master rbac]# kubectl apply -f rbac.yml
role.rbac.authorization.k8s.io/pod-reader configured
rolebinding.rbac.authorization.k8s.io/read-pods unchanged
[root@k8s-master rbac]# kubectl --kubeconfig=lulei.kubeconfig get deploy
NAME READY UP-TO-DATE AVAILABLE AGE
nginx 1/1 1 1 64d
[root@k8s-master rbac]# kubectl --kubeconfig=lulei.kubeconfig get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 64d
nginx NodePort 10.99.50.2 <none> 80:31332/TCP 64d[root@k8s-master rbac]# kubectl api-versions 查看哪些资源组
admissionregistration.k8s.io/v1
admissionregistration.k8s.io/v1beta1
apiextensions.k8s.io/v1
apiextensions.k8s.io/v1beta1
apiregistration.k8s.io/v1
apiregistration.k8s.io/v1beta1
apps/v1拿着上面lulei.kubeconfig就可以使用kubectl命令连接集群了
总结

当使用kucetl调用其api或者使用ui其实都是向api server组件发送的请求。
提取出证书里面的CN字段,该字段作为你的用户名。也就是从证书当中提取出用户名 "CN": "lulei",
- kind: User
name: lulei也可以基于组 "O": "k8s"
使用 ClusterRoleBinding 可以对整个集群中的所有命名空间资源权限进行授权;以下 ClusterRoleBinding 样例展示了授权 manager 组内所有用户在全部命名空间中对 secrets 进行访问
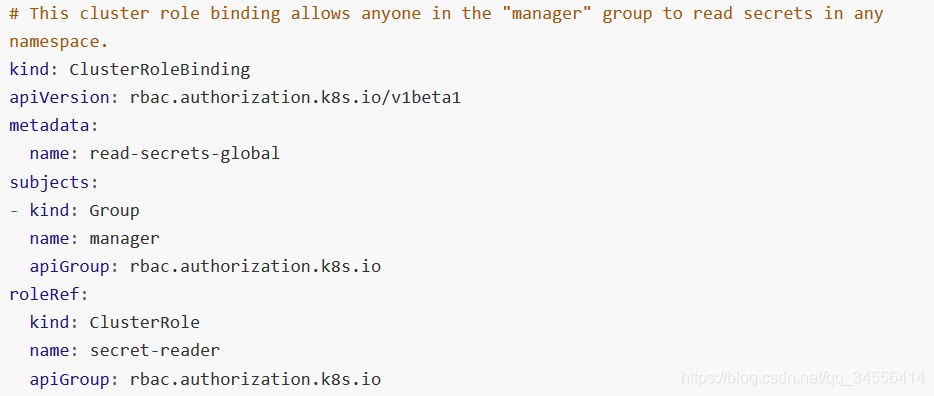
去验证你的身份是不是有效的,也就是你的证书是不是CA颁发的,验证客户端证书没问题进行下一个阶段的授权,也就是创建RBAC,授权之后可以访问。
使用kubeconfig还需要注意用户已经经过授权(如RBAC授权),上述例子中用户的证书中CN字段为"CN": "lulei",kube-apiserver 预定义的 RoleBinding read-pods 将User lulei 与 Role pod-reader 绑定,该 Role 授予了调用kube-apiserver 相关 API 的权限。
目录 返回
首页